Russia Began Setting Stage for Cyberattacks Against Ukraine a Year Ago
The Kremlin’s cyber warriors began working to gain a foothold in Ukrainian government and critical infrastructure networks a year before the invasion, according to a report issued by Microsoft today.
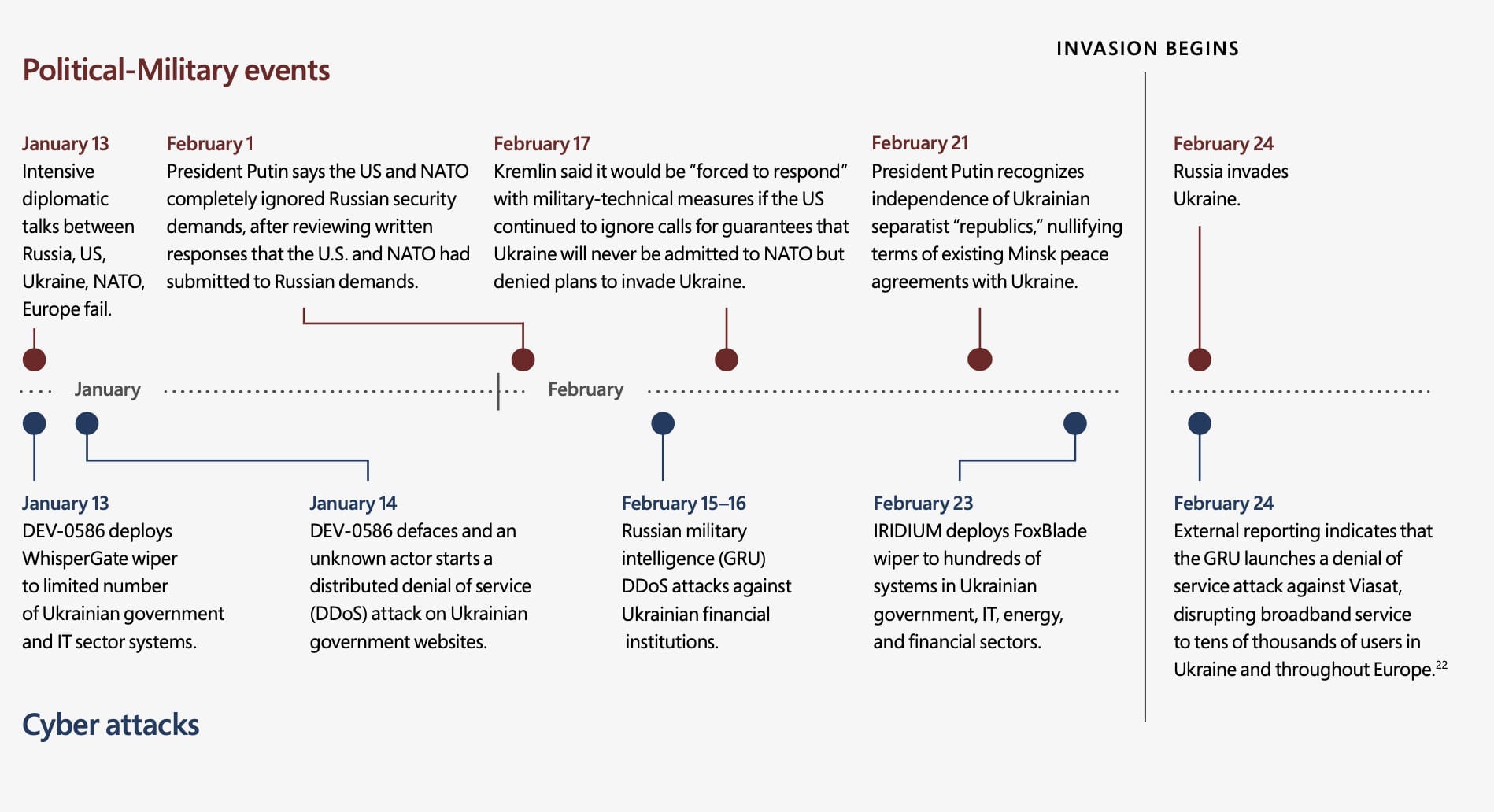
Russia began preparing for its conflict with Ukraine as early as March last year when the Kremlin’s cyber warriors worked to gain a foothold in Ukrainian government and critical infrastructure networks, according to a report issued by Microsoft today, which also notes that cyberattacks against Ukraine have been more “relentless” and widespread than previously reported.
Last March and April, as Russian troops first began amassing near the border with Ukraine and Crimea, Russian hackers were making moves to gain access to targeted systems that could yield intelligence about Ukraine’s military and the country’s partnerships with NATO member states.
For example, the Russian actor known as Nobelium — which was behind the SolarWinds campaign in the US in 2020 — launched a large-scale phishing operation to secure access for future intrusions against Ukraine and NATO member countries such as the United States, the United Kingdom, Norway, Germany, and Turkey.
Other Russian groups subsequently targeted supply-chain vendors in and outside Ukraine, Microsoft reports. Nobelium attempted to access IT firms serving government customers in NATO member states to steal data from foreign policy organizations. A previously unknown hacking group with suspected ties to Russia’s military compromised an IT firm that had built resource management systems for Ukraine’s Ministry of Defense and organizations in the communications and transportation sectors. And toward the end of last year, suspected Russian cyber actors positioned themselves inside the networks of Ukrainian energy and IT providers that were later targeted with destructive attacks, including the IT service provider Kitsoft.
The hackers gained access to Kitsoft’s administrator panel and used the company’s credentials to deface government web sites that the company managed, before infecting Kitsoft’s network with a wiper malware designed to destroy data and render systems inoperable.
Although experts have pondered why Russian hackers have seemingly held back in launching full-scale destructive cyberattacks against Ukrainian infrastructure since the war broke out two months ago, Microsoft, which has been helping Ukraine detect and defend against digital attacks, says cyber assaults against Ukraine have nonetheless been “destructive and relentless.”
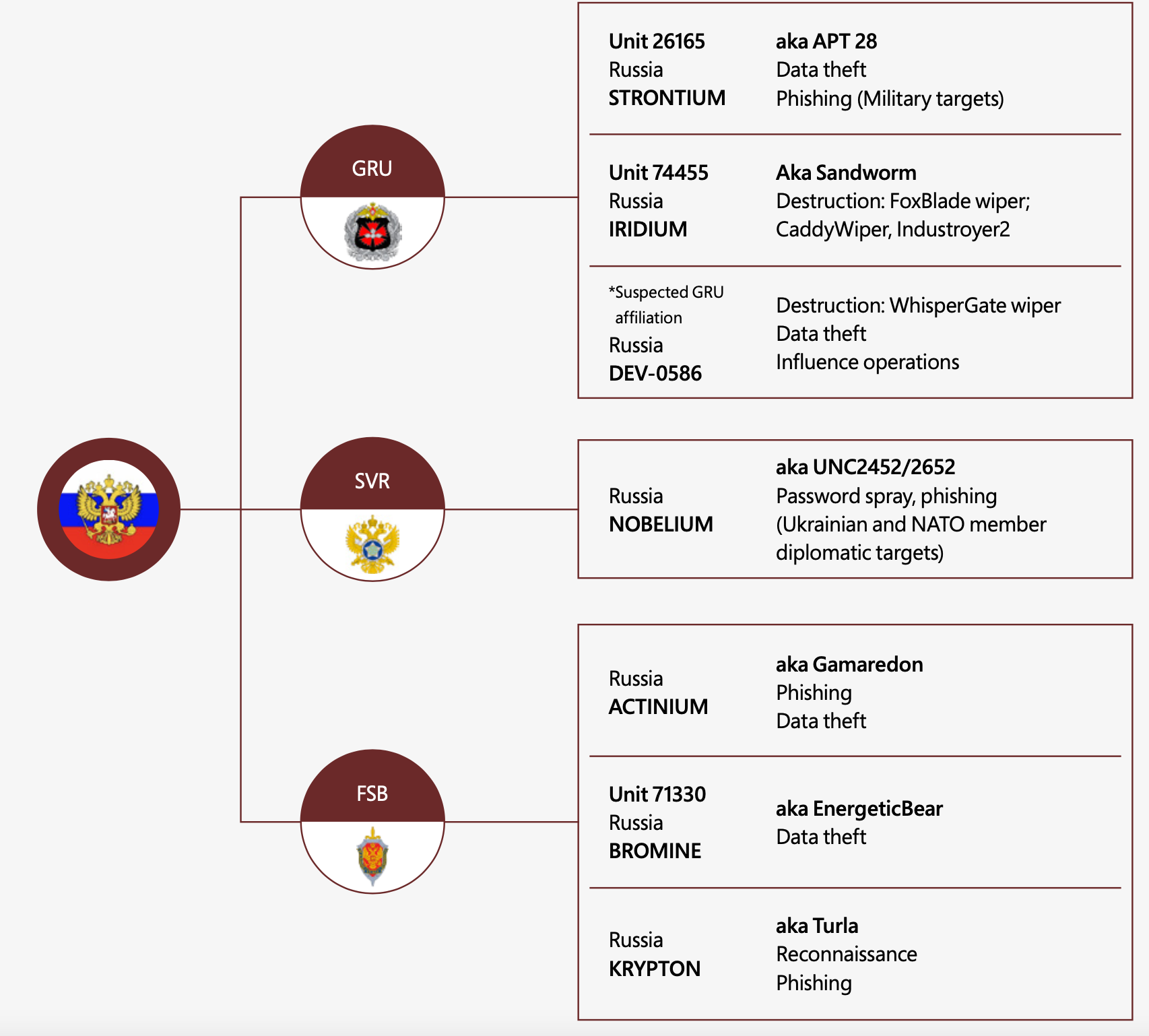
Since January, at least six separate Russian APT hacking groups have launched more than 237 operations against Ukrainian systems with the aim of collecting intelligence, eroding political will, and undermining the public’s trust in the government and the security of critical services. These include 40 destructive attacks using wiper malware that permanently destroyed files in about 300 systems across more than a dozen organizations in Ukraine — including government systems and systems in the IT, energy, agriculture, and financial sectors.
Microsoft has counted at least eight destructive malware families deployed on Ukrainian networks, including one designed to target industrial control systems, and has counted about two to three incidents a week since the eve of the invasion. The latter refers to a piece of malware known as Industroyer2, which the Slovakian-based security firm ESET says was discovered on the network of a regional Ukrainian electricity supplier just hours before it was set to cause damage to systems.
Furthermore, some cyber operations appear to be "strongly correlated and sometimes directly timed” with the Russian military’s kinetic operations to go after a shared target sets, although it’s unclear if the kinetic and cyber operations are actually coordinated.
“While we cannot speak to the level of coordination between disparate threat groups, combined, their activities appeared aimed at securing persistent access for strategic and battlefield intelligence collection or to facilitate future destructive attacks in Ukraine during military conflict,” Microsoft noted. At times, computer network attacks immediately preceded a military attack, “but those instances have been rare,” Microsoft said.
As an example, Microsoft cites Russian cyberattacks launched against a Ukrainian broadcasting company on March 1, the same day Russian missiles struck a TV tower in Kyiv. During the second week of the war, as Russian military forces prepared a ground attack against Kyiv, Russia-aligned threat actors attempted to compromise public information sources and communications infrastructure, likely with the aim of gaining insight into Ukrainian military operations. And a few weeks ago, Russian hackers targeted logistics providers and regional government organizations in advance of the Russian military refocusing its kinetic activity in eastern Ukraine. One group in particular conducted a destructive cyberattack against a transportation and logistics provider based in western Ukraine that would likely be involved in transporting Ukrainian supplies to conflict areas in the eastern part of the country and elsewhere. Similarly, Ukrainians officials have said that the Industroyer2 malware targeting a regional electrical supplier was likely aimed at cutting power to 2 million customers in at the same time that Russian military activities in the region surged.
In its Wednesday report, Microsoft detailed the type of attacks it has seen across Ukraine beginning last year and since the invasion. These included spearphishing campaigns designed to gain access to accounts of Ukraine-based foreign military advisors and humanitarian workers as well as military and regional government accounts. One hacking group staged a file encryptor — ransomware without the ransom demand — on the network of an agricultural firm. Microsoft says this was likely targeting grain production, which plays a major part in Ukraine’s export economy.
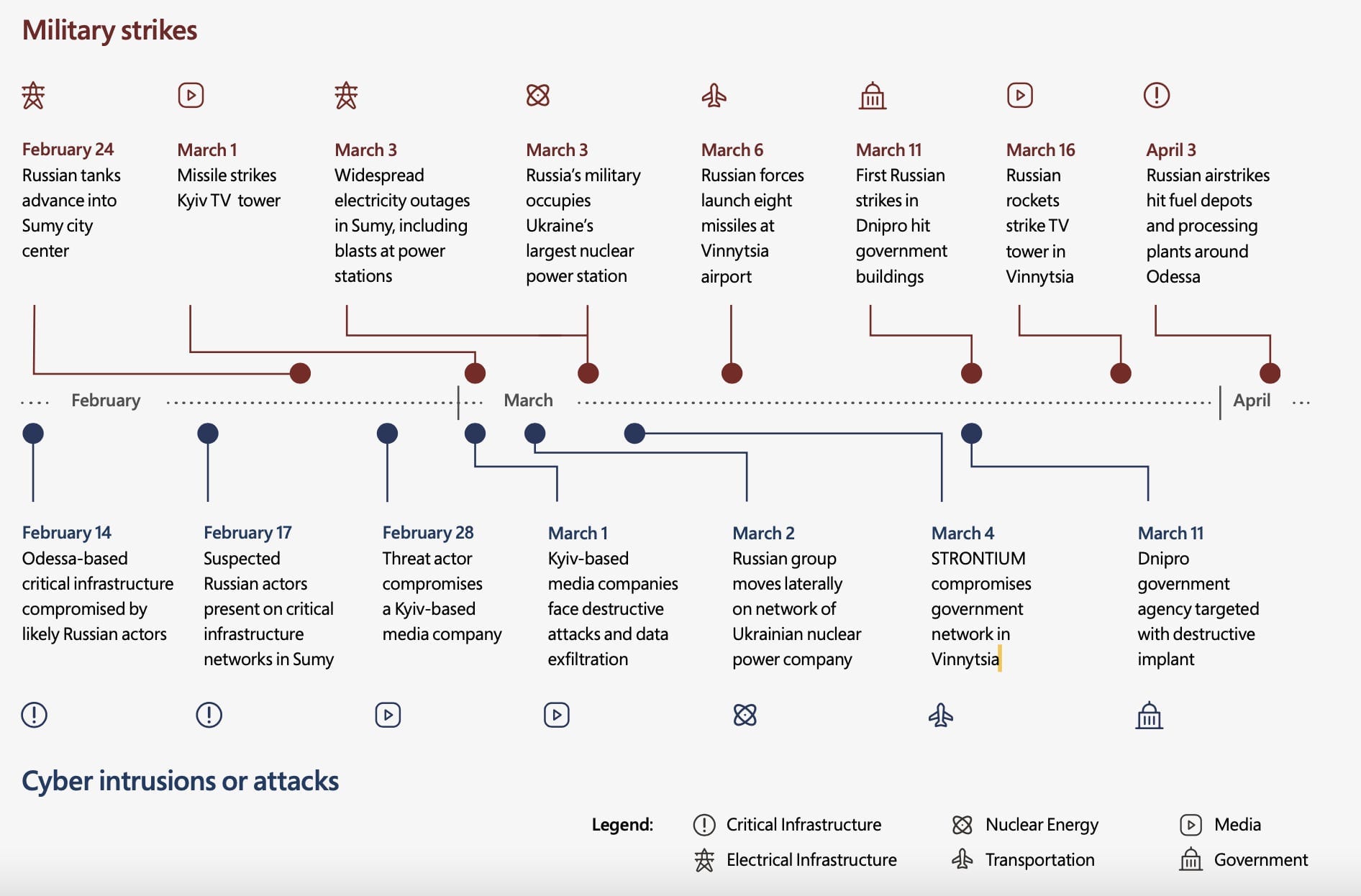
The hacking groups have used various methods to gain access — phishing campaigns, exploiting unpatched vulnerabilities in Microsoft Exchange servers, and compromising upstream IT service providers. They’ve also modified their malicious code with each deployment to thwart detection.
Despite all of this activity and the staging for attacks a year ago, Microsoft notes that the groups appear to be “operating with restraint in the execution of destructive attacks” by limiting their attacks to specific targeted networks.
In a briefing with reporters Wednesday morning, Victor Zhora, deputy chief of Ukraine's State Service of Special Communications and Information Protection, surprisingly said that despite the connoting threat, Russian cyberattacks against Ukraine appeared to have likely “reached their full potential,” suggesting that Russian attacks were unlikely to get more destructive than they have been until now.
Russian hackers “continue to be dangerous” he said, “but … I don't think they can scale their cyber warriors or they can use some completely new technologies that can attack Ukrainian infrastructure [and] …we are completely able to resist them.”
He subsequently clarified his remarks.
“If they wanted to arrange anything very destructive they had two months for this [already],” he said. They had ample opportunity to use the most destructive attacks they could devise, but they haven’t done so.
“[W]e shouldn’t underestimate Russian hackers, but we probably should not overestimate their potential since the potential isn’t growing now” he continued, and their financial resources for organizing such operations are now limited as well as the time to plan and conduct sophisticated operations that can take months to coordinate.
Related:
What We Know and Don’t Know about the Cyberattacks Against Ukraine - (updated)
Dozens of Computers in Ukraine Wiped with Destructive Malware in Coordinated Attack
Hackers Were in Ukraine Systems Months Before Deploying Wiper
Wiper in Ukraine Repurposed from WhiteBlackCrypt Ransomware
Inside the Cunning, Unprecedented Hack of Ukraine’s Power Grid
The Ukrainian Power Grid Was Hacked Again
If you like this story, feel free to share with others.
If you’d like to receive future articles directly to your email in-box, you can also subscribe: