Former Trenchant Exec Sold Stolen Code to Russian Buyer Even After Learning that Other Code He Sold Was Being "Utilized" by Different Broker in South Korea

The former executive of Trenchant who pleaded guilty this week to selling his company's software hacking tools to a zero-day broker in Russia, sold at least one of these tools to the Russian firm even after learning that a previous tool he sold the broker was being used by a South Korean broker – indicating that the stolen tools were being passed on to others downstream.
Peter Williams, the 39-year-old former executive of Trenchant, admitted to stealing at least eight software trade secrets from his former employer – court documents don't specify the nature of the stolen goods, but Trenchant creates and sells zero-day exploits and other hacking tools exclusively to the US government and its allies and the Russian buyer is identified as a broker that buys and sells zero-day exploits.
Williams admitted to the FBI that "even after he recognized code he wrote and sold" to the Russian buyer was being "utilized" by a South Korean broker, he still sold at least one other Trenchant tool to the Russian buyer. This suggests that Williams may have written some of the code he stole from Trenchant, though the document doesn't elaborate on this.
In perhaps the most remarkable part of his crime spree, Williams continued to sell exploits to the Russian buyer this year even while the FBI was investigating the theft of code from Trenchant. In June 2025, he signed an agreement with the Russian buyer to sell stolen code for $500,000 and transmitted the code to the buyer just days before he met with the FBI to discuss their investigation in to the theft of Trenchant's code.
Trenchant is in the business of selling zero-day exploits and other hacking tools exclusively to the US government and select allied governments (which likely include Williams' own Australian government). When the FBI finally confronted Williams with his crimes, he estimated to the bureau that at least two of the software tools he sold to the Russian buyer amounted to a loss of about $35 million for Trenchant.
These new details appear in a court document published through the US District Court of the District of Columbia, where Williams pleaded guilty this week. The so-called Statement of Offense includes a lot of information previously revealed by prosecutors during the court hearing on Wednesday when Williams pleaded guilty – information that I already reported in a story for Wired – but it also includes some new details.
As previously reported, Williams had worked for the Australian Signals Directorate, during the 2010s. The ASD is Australia's equivalent to the US National Security Agency and, like the latter agency, uses software exploits to hack into computers to conduct espionage and sabotage. At some point he left the ASD and beginning in at least 2016, he began working for a company that later became Trenchant.
Trenchant, or L3Trenchant as it's formally known, was formed through the merging of two Australian firms – Azimuth and Linchpin Labs – after the US-based defense contractor L3Harris acquired the two companies in 2018. Azimuth was well-regarded in the intelligence community for creating valuable zero-day exploits and other hacking tools for the US and select allies.
Since 2023, Williams had been in the US on a work visa, working out of Trenchant's DC offices, and he became general manager of the company in October 2024. Notably, that's the same month that Trenchant learned that some of its valuable software tools had leaked from its secure network and was in the hands of a foreign broker. The document doesn't indicate who informed the company, but it's likely it was the FBI.
Trenchant confirmed that a broker outside the US was selling a component of one of its software products and immediately launched an internal investigation, with Williams overseeing a trusted company investigator who was conducting the inquiry. The investigation concluded that Trenchant's secure network had not been compromised – "outside of a former employee who, while employed, had improperly accessed the internet from an air-gapped device.”
Trenchant keeps its sensitive code stored on a secure air-gapped network that is not connected to the internet, to prevent outsiders from breaching the network and siphoning the company's valuable assets.
In November the company provided the FBI with the results of its internal inquiry. But the FBI was conducting its own investigation, conducting interviews with Trenchant employees. In one interview that Williams conducted with the FBI in July 2025, he said the most probable way for someone to steal code from Trenchant's secure network without triggering internal indications of compromise was for someone with access to the secure network to download material from the network and transfer it to an air-gapped device like a mobile phone or external drive. Two months later when the FBI confronted Williams with evidence of his crimes, he admitted that this was how he stole the code from Trenchant – downloading it from the company's network in DC and in Sydney, Australia, using a portable hard drive, then transferring it to a personal computer where he removed any identifying information that pointed specifically to himself or to his company before transmitting it to his Russian buyer.
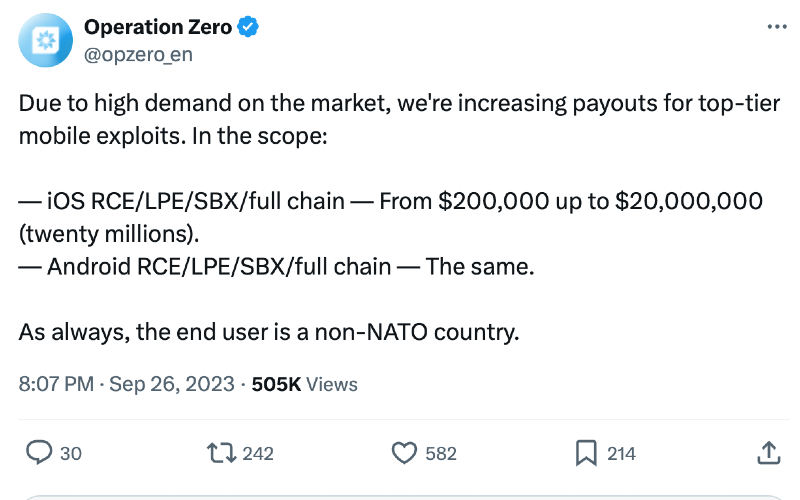
Court documents don't identify the Russian company, but at Wednesday's hearing, a prosecutor noted that in September 2023 the company had published a social media post announcing that it was increasing payouts for some mobile phone exploits ranging from $200,000 to $20 million. This matches a post that a Russia-based company called Operation Zero published on X on September 26, 2023. Operation Zero describes itself as the “only Russian-based zero-day vulnerability purchase platform." As the post on X notes, Operation Zero planned to purchase the exploits for a "non-NATO country," suggesting the Russian government or another non-NATO country was the intended recipient.
Williams began his criminal spree in April 2022 when he created an email account under the pseudonym "John Taylor" and contacted the Russian firm through encrypted communication to negotiate a price to sell his first exploit. He signed a contract for about $240,000 to be paid in cryptocurrency.
It's not clear if the buyer knew the real identify of John Taylor and his circumstances – that he worked for a company that makes zero-day exploits and was stealing from his employer, and that he had previously worked for the Australian intelligence community.
The buyer agreed to make additional payments once it confirmed that the exploit worked as well as more payments if Williams updated the software to maintain its efficacy after the initial sale. A zero-day exploit can stop working if the maker of the software the exploit attacks patches the vulnerability the exploit targets or distributes some other update to the software that impacts the efficacy of the exploit. Exploit sellers will sometimes devise a way to bypass the patch or make some adjustments to the exploit to allow it to continue to work for the customer.
Between April 2022 and June 2025, Williams was in regular communication with the Russian buyer and entered into separate written contracts for each of the tools he sold, signing each contract under the name John Taylor. The contracts promised an upfront payment once the buyer determined the code worked, and then additional payments if the code continued to work over time. Williams agreed to provide at least three months of follow-on support at a price of $10,000 a month. In another example, Williams signed a contract on December 4, 2023 that would pay him $2 million for one of the stolen trade secrets. The court document notes that this amount “was consistent with a public bug bounty” that the company had advertised in September 2023.
Notably, Williams continued his crimes even while another employee at Trenchant was reportedly fired for stealing zero-day exploits for the Chrome browser from Trenchant and leaking them – a crime he says he didn't commit. As reported earlier this month by Tech Crunch, last February the worker says he was called into Trenchant's London office for a team-building exercise, but when he arrived he was ushered into a meeting room for a video call with Williams. Williams said the company suspected the employee of moonlighting for another company and seized his electronics and suspended him. He was subsequently fired, though Williams did not give a reason. The employee only learned from other workers later that they company suspected he had stolen the zero-day exploits.
It's not clear if the trade secrets Williams sold to the Russian buyer were zero-day exploits for Chrome, but the details and timing of the events suggest the possibility that Williams may have engaged in some misdirection to pin blame on the employee for stealing exploits that he himself stole.
In any case, months later in June 2025, while the FBI was investigating the theft of secrets from Trenchant, Williams signed a contract with the Russian buyer to provide one of the stolen products for $500,000 and delivered the item to the Russian firm that same month. He agreed to receive a bulk payment of $300,000 and two additional payments of $100,000 each, with the last payment being scheduled to arrive in September 2025. According to the court document, after he received the first payment, he transferred it to one of his bank accounts in August. It was that month, during another interview with the FBI, that agents confronted him with evidence of his crimes, leading him to confess. Williams subsequently resigned from his job at Trenchant.
Each time the Russian buyer paid Williams in cryptocurrency, he laundered it through several cryptocurrency accounts before using a virtual currency exchange to convert it into fiat currency. According to the government, Williams used an exchange service that does not require users to create an account to use it, and also generally does not collect customer identity information unless a specific transaction is flagged for further review. Once the money was converted into fiat currency, Williams deposited into accounts that he had in the US and Australia.
In total, the contracts promised Williams more than $4 million, though court documents don't indicate the total amount he actually collected. They say only that he received upfront payments in cryptocurrency worth in excess of $1.3 million, raising questions about whether he actually received more than this.
He used the proceeds to put a down payment on a house in northwest Washington, DC earlier this year. Though the court document doesn't say when he purchased the home or for how much, online records show that the five-bedroom row house sold in June this year – shortly before Williams' July interview with the FBI – for $1.56 million.
Williams has agreed to pay restitution of $1.3 million, and to cover this, he has agreed to forfeit the house as well as dozens of luxury items that the government says he purchased with proceeds from the sale of the stolen software. This includes twenty-two watches – many of them from the luxury brands Rolex, Longines, and Tag Heuer but some of them fake replica watches – several pieces of women's diamond jewelry and designer clothing. He has also agreed to forfeit funds contained in more than half a dozen bank and cryptocurrency accounts he has in the US and Australia.
In his plea agreement, Williams acknowledged that in stealing Trenchant's software and selling it to the Russian buyer he had harmed both the intelligence community of Australia and the US.